"Cloud" is a metaphorical statement of the Internet and the Internet. In the past, telecommunications networks were often represented by clouds in the diagram, and later used to represent the abstraction of the Internet and underlying infrastructure.
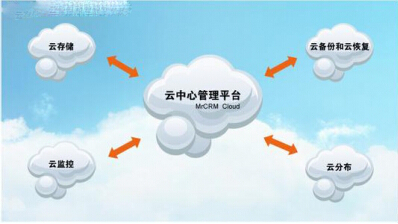
"Cloud Security" is based on the Internet of Things model and adopts cloud storage technology to meet the needs of modern security. Specific implementation refers to the integration of technologies such as video surveillance, access control, RFID radio frequency identification, intrusion alarms, fire alarms, SMS alarms, and GPS satellite positioning through “clouds†through cluster applications, grid technologies, and distributed file system functions. Work collaboratively to exchange information and communicate and complete smart identification, location, tracking and monitoring of security management. Users can perform 24-hour seamless remote monitoring through C/S, B/S, and mobile device clients. With the growing demand for multi-level inter-regional large-scale networking and massive data processing in social security video surveillance systems, cloud technology is also increasingly used in video surveillance systems.
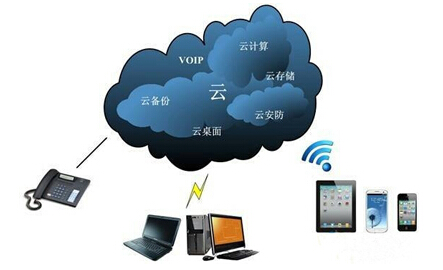
When it comes to "cloud security," we cannot but mention cloud storage. This is a highly tempting storage technology. Cloud storage can achieve complete virtualization of storage, greatly simplify the application process, save customers' construction costs, and provide stronger storage and sharing capabilities. All devices in the cloud storage are completely transparent to users. Any authorized user can connect to the cloud storage through an access line anywhere for space and data access. Users do not need to care about the storage device model, quantity, network structure, storage protocol, application interface, etc., and the application is simple and transparent. For users, cloud storage does not refer to a specific device, but refers to a collection of many storage devices and servers. Instead of using a storage device, users use cloud storage instead of using a data access service brought by the entire cloud storage system. So strictly speaking, cloud storage is not a storage but a service.
With the development of large-scale network monitoring and the increasing popularity of high-definition surveillance, the massive amount of video data that needs to be stored is impacting the storage system in a flooding manner, which not only imposes higher requirements on the capacity of the storage device, read/write performance, and reliability. Monitor the emergence of cloud storage, break through the performance and capacity bottlenecks of traditional storage methods, enable cloud storage providers to connect a large number of different types of storage devices in the network to form exceptionally strong storage capacity, and achieve linear expansion of performance and capacity. The storage of data has become possible, allowing companies to have the storage capacity equivalent to a whole piece of cloud and successfully solve the storage problem. Monitoring the emergence of cloud storage at the same time enhances the competitiveness of users and manufacturers.
Video surveillance as the main branch of the security field, the amount of data on the network bandwidth consumption is very large, for the time being, I am afraid not fully equipped with the conditions of data center, cloud security technology in the field of monitoring applications will also come a long way Distance, but with the rapid development of network technology, the obstacles affecting its promotion will be fundamentally resolved, and cloud security will have a bright future.

"Cloud Security" is based on the Internet of Things model and adopts cloud storage technology to meet the needs of modern security. Specific implementation refers to the integration of technologies such as video surveillance, access control, RFID radio frequency identification, intrusion alarms, fire alarms, SMS alarms, and GPS satellite positioning through “clouds†through cluster applications, grid technologies, and distributed file system functions. Work collaboratively to exchange information and communicate and complete smart identification, location, tracking and monitoring of security management. Users can perform 24-hour seamless remote monitoring through C/S, B/S, and mobile device clients. With the growing demand for multi-level inter-regional large-scale networking and massive data processing in social security video surveillance systems, cloud technology is also increasingly used in video surveillance systems.

When it comes to "cloud security," we cannot but mention cloud storage. This is a highly tempting storage technology. Cloud storage can achieve complete virtualization of storage, greatly simplify the application process, save customers' construction costs, and provide stronger storage and sharing capabilities. All devices in the cloud storage are completely transparent to users. Any authorized user can connect to the cloud storage through an access line anywhere for space and data access. Users do not need to care about the storage device model, quantity, network structure, storage protocol, application interface, etc., and the application is simple and transparent. For users, cloud storage does not refer to a specific device, but refers to a collection of many storage devices and servers. Instead of using a storage device, users use cloud storage instead of using a data access service brought by the entire cloud storage system. So strictly speaking, cloud storage is not a storage but a service.
With the development of large-scale network monitoring and the increasing popularity of high-definition surveillance, the massive amount of video data that needs to be stored is impacting the storage system in a flooding manner, which not only imposes higher requirements on the capacity of the storage device, read/write performance, and reliability. Monitor the emergence of cloud storage, break through the performance and capacity bottlenecks of traditional storage methods, enable cloud storage providers to connect a large number of different types of storage devices in the network to form exceptionally strong storage capacity, and achieve linear expansion of performance and capacity. The storage of data has become possible, allowing companies to have the storage capacity equivalent to a whole piece of cloud and successfully solve the storage problem. Monitoring the emergence of cloud storage at the same time enhances the competitiveness of users and manufacturers.
Video surveillance as the main branch of the security field, the amount of data on the network bandwidth consumption is very large, for the time being, I am afraid not fully equipped with the conditions of data center, cloud security technology in the field of monitoring applications will also come a long way Distance, but with the rapid development of network technology, the obstacles affecting its promotion will be fundamentally resolved, and cloud security will have a bright future.
Shower And Bath Valve,Bath Valve,Bathtub Valve,Tub And Shower Faucets
Moon Shower Sanitaryware Co.,Ltd , https://www.moonshowerglobal.com